Getting shafted on my broadband
polkfarmboy
Posts: 5,703
My net bills as of recent are sky high and now I find myself being overcharged for going over my bandcap. The thing is that I am not downloading anything and today I used up 10 gig for being on polk and facebook ?
Post edited by polkfarmboy on
Comments
-
Wow, you even managed to break your Internet...
Sorry, couldn't resist -
Thats why those limited data plans suck.
-
HTH do you use 10Gigs just browsing?"Appreciation of audio is a completely subjective human experience. Measurements can provide a measure of insight, but are no substitute for human judgment. Why are we looking to reduce a subjective experience to objective criteria anyway? The subtleties of music and audio reproduction are for those who appreciate it. Differentiation by numbers is for those who do not".--Nelson Pass Pass Labs XA25 | EE Avant Pre | EE Mini Max Supreme DAC | MIT Shotgun S1 | Pangea AC14SE MKII | Legend L600 | BlueSound Node 3 - Tubes add soul!
-
HTH do you use 10Gigs just browsing?
Hi-Rez **** uses copious amounts of bandwidth...
*cough* uhhh, I read that somewhere *cough*:eek:So, are you willing to put forth a little effort or are you happy sitting in your skeptical poo pile?
http://audiomilitia.proboards.com/ -
Is your wifi network secure? Perhaps a neighbor of yours has been enjoying some HD streaming videos on your behalf...2 Channel - Polk SDA-2BTL, Carver TFM-35, Peachtree iDAC, Qobuz streamed via Episode Lynk using bubble UPnP server
-
I just called the net provider and he said that last month on the off peak (free) hours there was 180 gig downloaded after 12 pm. Some one is for sure jacking my net and I will find out after some research
-
ambiophonics wrote: »Is your wifi network secure? Perhaps a neighbor of yours has been enjoying some HD streaming videos on your behalf...
I used that 24 character wep key? I thought that would be secure enough -
polkfarmboy wrote: »I used that 24 character wep key? I thought that would be secure enough
I would suggest using WPA or WPA2 and also changing the default gateway, subnet mask and admin logon for your router. All easy things to do. Also constantly check what devices are connected and if you find one thats not yours try to find the MAC address of it and then put it in your MAC filtering list so it can no longer connect even if it has valid credentials...
That or just get the MAC addresses of all the legit pieces of equipment and put those in and dont allow any others..."....not everything that can be counted counts, and not everything that counts can be counted." William Bruce Cameron, Informal Sociology: A Casual Introduction to Sociological Thinking (1963) -
WEP is garbage.
WPA2 as well as MAC filtering here. No one uses my network.
-
WEP is garbage.
WPA2 as well as MAC filtering here. No one uses my network.
Same Here!Michael
In the beginning, all knowledge was new!
NORTH of 60° -
EndersShadow wrote: »I would suggest using WPA or WPA2 and also changing the default gateway, subnet mask and admin logon for your router. All easy things to do. Also constantly check what devices are connected and if you find one thats not yours try to find the MAC address of it and then put it in your MAC filtering list so it can no longer connect even if it has valid credentials...That or just get the MAC addresses of all the legit pieces of equipment and put those in and dont allow any others...
How do you do this? Not very computer savvy. -
While it may be somebody sharing your wifi, you may also have somebody using your computer as a server for some type of file sharing.
-
While it may be somebody sharing your wifi, you may also have somebody using your computer as a server for some type of file sharing.
How can you find that out?
I took out the router and went into the cable modem and reset everything and then done a speed test and its still down by around 12 gig -
What do you use for Virus/Spyware monitoring? Check what processes are running, look for unusual ones with names of which you may not recognize.
-
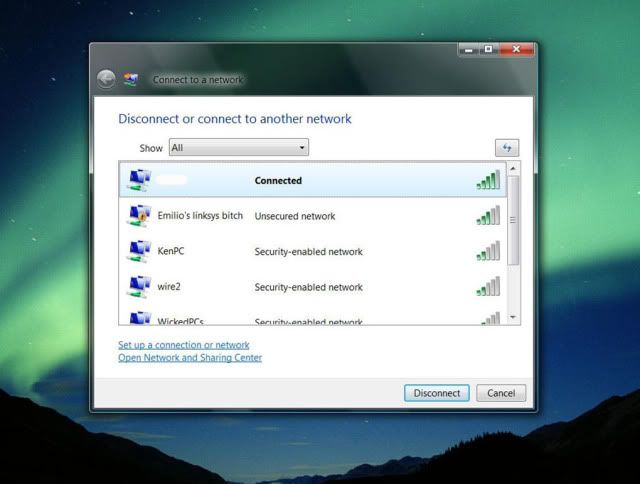
Folks that can't hack into my wireless use my neighbors, Emilio's linksys ****.

 Salk SoundScape 8's * Audio Research Reference 3 * Bottlehead Eros Phono * Park's Audio Budgie SUT * Krell KSA-250 * Harmonic Technology Pro 9+ * Signature Series Sonore Music Server w/Deux PS * Roon * Gustard R26 DAC / Singxer SU-6 DDC * Heavy Plinth Lenco L75 Idler Drive * AA MG-1 Linear Air Bearing Arm * AT33PTG/II & Denon 103R * Richard Gray 600S * NHT B-12d subs * GIK Acoustic Treatments * Sennheiser HD650 *
Salk SoundScape 8's * Audio Research Reference 3 * Bottlehead Eros Phono * Park's Audio Budgie SUT * Krell KSA-250 * Harmonic Technology Pro 9+ * Signature Series Sonore Music Server w/Deux PS * Roon * Gustard R26 DAC / Singxer SU-6 DDC * Heavy Plinth Lenco L75 Idler Drive * AA MG-1 Linear Air Bearing Arm * AT33PTG/II & Denon 103R * Richard Gray 600S * NHT B-12d subs * GIK Acoustic Treatments * Sennheiser HD650 * -
SCompRacer wrote: »Folks that can't hack into my wireless use my neighbors, Emilio's linksys ****.


Hahahahaha! I like what you did there. -
How do you do this? Not very computer savvy.
Its going to vary manufacture to manufacture. There should be a location where your router will show a list of all the device names and MAC addresses of items connected to your router at any given time.
Check your manual."....not everything that can be counted counts, and not everything that counts can be counted." William Bruce Cameron, Informal Sociology: A Casual Introduction to Sociological Thinking (1963) -
polkfarmboy wrote: »How can you find that out?
I took out the router and went into the cable modem and reset everything and then done a speed test and its still down by around 12 gig
Well realistically if your in this situation, I would download Avast, Spybot, Malwarebytes along with the new definitions (dont install them yet). Boot into safe mode without networking. This will help ya when you run your scans. Once your booted into safe mode, install all three of those programs and run scans with them (after loading the new definitions).
See what you get and lets go from there.
HiJackThis is another good program for finding this kinda stuff and locking your computer down but not exactly user friendly so I wouldnt suggest it unless your decent with computers."....not everything that can be counted counts, and not everything that counts can be counted." William Bruce Cameron, Informal Sociology: A Casual Introduction to Sociological Thinking (1963) -
Hahahahaha! I like what you did there.
Really, it was real. Only photoshop was eliminating my network name.Salk SoundScape 8's * Audio Research Reference 3 * Bottlehead Eros Phono * Park's Audio Budgie SUT * Krell KSA-250 * Harmonic Technology Pro 9+ * Signature Series Sonore Music Server w/Deux PS * Roon * Gustard R26 DAC / Singxer SU-6 DDC * Heavy Plinth Lenco L75 Idler Drive * AA MG-1 Linear Air Bearing Arm * AT33PTG/II & Denon 103R * Richard Gray 600S * NHT B-12d subs * GIK Acoustic Treatments * Sennheiser HD650 * -
I ran the malware bytes prog and nothing came up.
-
That's awesome, Rich.
 Jay
Jay
SDA 2BTL * Musical Fidelity A5cr amp * Oppo BDP-93 * Modded Adcom GDA-600 DAC * Rythmik F8 (x2)
Micro Seiki DQ-50 * Hagerman Cornet 2 Phono * A hodgepodge of cabling * Belkin PF60
Preamp rotation: Krell KSL (SCompRacer recapped) * Manley Shrimp * PS Audio 5.0 -
SCompRacer wrote: »Really, it was real. Only photoshop was eliminating my network name.
I saw that, I liked the way you worded it. -
What router do you have? You should be able to log into it and see what devices are running off of it.
And 180gb of Data download? Even I don't run anywhere near that. -
What sort of distance is "safe" from having neighbors being able to tap into a home's wireless network ??
-
polkfarmboy wrote: »How can you find that out?
I took out the router and went into the cable modem and reset everything and then done a speed test and its still down by around 12 gig
Go into the network control panel and see the amount of sent data under your current connection. Unless you upload a lot of files this should be realitively small. -
So today my bandwidth used is only 400 mb compaired to the 5,6 and 8 gigs I have been getting hit with. My wifi is off so its for sure being jacked
-
Now you've done it. Patrick was running the forum on your system.>
>
>This message has been scanned by the NSA and found to be free of harmful intent.< -
Do you really need the Wi-Fi? I only ask because you say it's off now. If not, leave it off.
Otherwise:
Don't broadcast your SSID.
Use MAC filtering to only allow your own devices.
WPA2 encryption, with the longest randomly generated password allowed.
Limit the number of connections to the amount of devices you have.
If someone is really determined and has the knowledge, they can still get in. But this will stop most, as they will move on to an easier target. WEP can be broken in minutes with freely available programs. -
Not broadcasting the SSID doesn't really do much truthfully. In fact, it actually causes devices like your laptop where the SSID is stored to adhere the network name to part of it's packets, so that when you are in a public place looking to connect to a new Wi-Fi signal, you are actually inadvertently broadcasting the name of your home network around.
From: http://www.howtogeek.com/howto/28653/debunking-myths-is-hiding-your-wireless-ssid-really-more-secure/ -
Not broadcasting the SSID doesn't really do much truthfully. In fact, it actually causes devices like your laptop where the SSID is stored to adhere the network name to part of it's packets, so that when you are in a public place looking to connect to a new Wi-Fi signal, you are actually inadvertently broadcasting the name of your home network around.
From: http://www.howtogeek.com/howto/28653/debunking-myths-is-hiding-your-wireless-ssid-really-more-secure/
Like I said, if someone's determined, they can get in. Why would I care if my laptop is leaking the name of my network when I'm miles from home? How would that help anyone connect easier than just broadcasting it? WPA2 is the best deterent, and I included it.











